Put Security First with a Holistic Cybersecurity Strategy
Our Focus
We provide a fully-integrated cybersecurity platform that incorporates compliance, detection, and response seamlessly... like no other solution.
Imagine having the peace of mind that comes with knowing that your company’s data is truly safe. No worries. No hassles. No potential ransomware attacks. Just complete and seamless protection. On any given day, our cybersecurity platform monitors more than 540TB of traffic, inspects 346M connections, analyzes 86M SMTP / 172M HTTP connections, and fingerprints over 100K devices.
Our ironclad cybersecurity offerings can bring a little calm to your life.
Inspirica IT provides a broad array of cybersecurity services to protect your enterprise. We can manage your entire network security, but often partner with your existing IT and/or security personnel. We work with most major advanced security vendors and can help you design the most advanced security services, policies and processes.
A fully-integrated security solution, deployable in hours:
Everything that makes healthcare more efficient, every access point, new device, or algorithm, for every positive there’s a negative: risk and vulnerability.
Tom Ridge, First Secretary
US Department of Homeland Security

Rapid Deployment: Security appliances are deployed and ready to activate as soon as they are powered on and connected
Instant Configuration: Once connected, appliances immediately start monitoring your network, without lenghty configuration
Auto-updating: Appliances are designed to auto-update and auto-heal, installing the latest features and capabilities
Community Threat Intelligence: appliances automatically obtain threat intelligence from the cloud, including IOC related to domains, file hashes, URL/URI, and more
Compliance
Practical approaches and solutions to help you achieve and maintain compliance.
- Cybersecurity Maturity Manager
- Cybersecurity Risk Register
- Policy Exception Manager
- Threat Tracker
- Threat Intelligence Framework
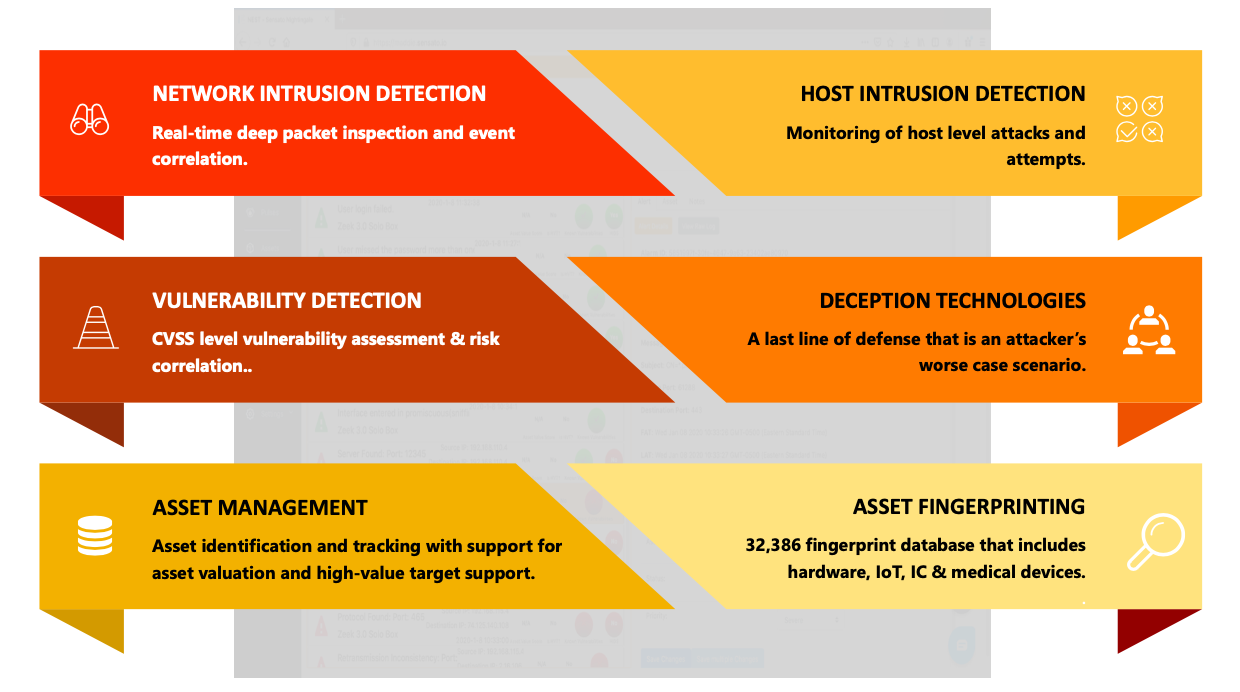
Detection
Solutions that streamline your ability to detect attacks, breaches and more.
- Asset Fingerprinting & Management
- Host Intrusion Detection
- Honeypot Technology
- Network Intrusion Detection
- Vulnerability Detection
- Open Platform
- Threat Intelligence Framework
Response
Industry-leading tools and practices, based on the real-world critical response, help you not just respond but also contain, fight back and recover at the speed of the attack.
- Coordinated Response Between Systems
- Orchestrate Organizational Threat Response
- Centralize your IR Protocols
- Community Threat Intelligence
Let Inspirica IT Protect Your Enterprise
Knowing that your company’s data is truly safe is something we all need.
No worries. No hassles. No potential ransomware attacks. Just complete and seamless protection.
We would love to show you how our ironclad cybersecurity offerings can bring a little calm to your life.
Call Inspirica IT for a quick chat to learn how we might serve your needs.
Contact Inspirica IT today:


